
Securely Deleting your Data (why you need it and how to do it)
Deleting data off of your flash drive or computer is not as cut-and-dry as most would likely assume. In the past we've spoken about file systems and how they organize data on all your modern storage devices. When you delete a file from your flash drive or any block storage device, it is not necessarily the file that is cleaned from the drive. Instead it is the index, or location, of that data that is being deleted so that it is no longer readily available. However that data still exists, in some capacity, on your flash drive or computer.
Even in situations where you have completely erased the file and file location from your device,similar types of problems persist; physical traces of your data literally remain imprinted on the apparatuses that make your device work. With the help of specialized tools, an expert could theoretically recover erased data by inspecting the physical positioning of parts inside your device.
Some have theorized, for example, that data could remain (long after intended use) on a flash memory device as a result of our inability to specifically target sections on a flash memory device. While the process for this would be complex, protecting against it is actually pretty simple.
So, I'm going to help guide you through the process of securely erasing data from your flash drive or computer to mitigate the risk of someone retrieving your information after you want it gone!
Standards of Data Erasure
Vulnerabilities like these have long existed in the memory world and while our data is probably more secure now than it was at the advent of digital data storage, data predator's methods have also increased in sophistication and range.
This brings us to one of the earliest attempts to address the concern for securely deleting your data: The Gutmann Method. In 1996 Peter Gutmann published his paper, "Secure Deletion of Data from Magnetic and Solid-State Memory" through the University of Auckland in New Zealand. To condense his points, Mr. Gutmann asserted that a secure delete from a block memory device would require ~35 write/erase cycles (using a specialized pattern) to fully remove a given piece of data from a drive. The logic being that after so many write/erase cycles, one could be assured that even the "ghost" files no longer existed regardless of whether someone was able to restore the index or find the original location of the data.
In the modern era, The Gutmann Method is outdated primarily because it was designed for devices that used an older encoding method named MFM (modified frequency modulation) however Mr. Guttmann himself remains an important voice in this industry speaking on privacy concerns in the digital age. At the time, the US government had just started to develop its own standards among its agencies for data protection. Peter's was, by a significant measure, the most extensive.
Peter Guttmann's method for a secure delete caused waves, eventually leading to many other organizations and experts developing their own approximations. The Department of Defense for example, advises using 3 overwrite cycles with a unique pattern they devised. The National Institute of Standards and Technology uses a single overwrite pass with a classified pattern unique to them. Notably, the NSA (National Security Agency) recommends 0 overwrite cycles and instead recommends destroying the device entirely for a truly secure delete.
Performing your own Secure Delete
In order to perform the Gutmann or any other method of effective write/erase cycles, you'll need the help of a program or application that can perform the procedure on your drive.
After a bit of research and testing, Eraser is the crowd pick for a few reasons. Its a great pick firs and foremost because its a totally free software that doesn't attempt to give you any extra applications or pesky toolbars when you download it. What's more is that Eraser also offers you tons of options like scheduling secure deletes ahead of time and specifying certain drives and partitions to interact with.
Follow along below:
Once you've downloaded and launched Eraser from their website, right click anywhere in the white "Erase Schedule" area.
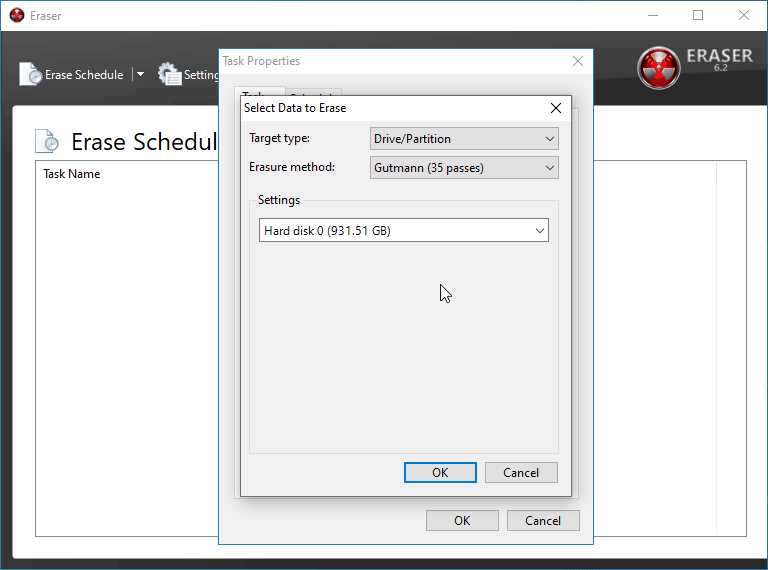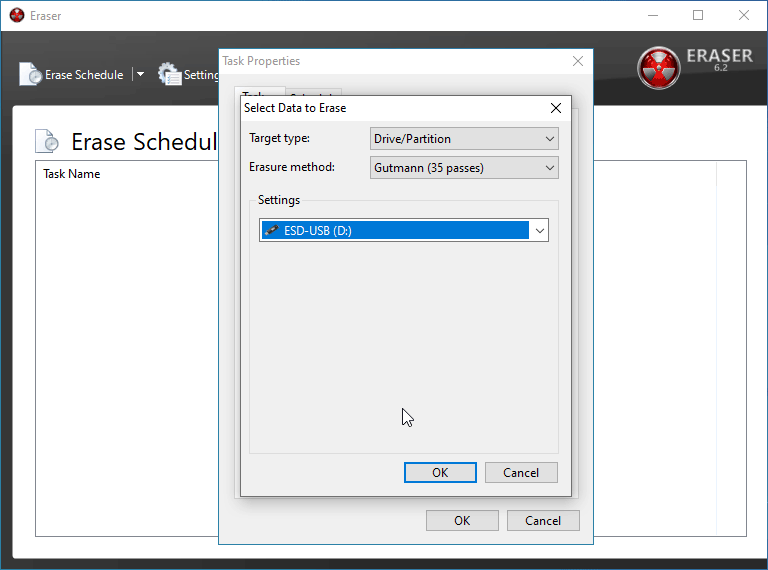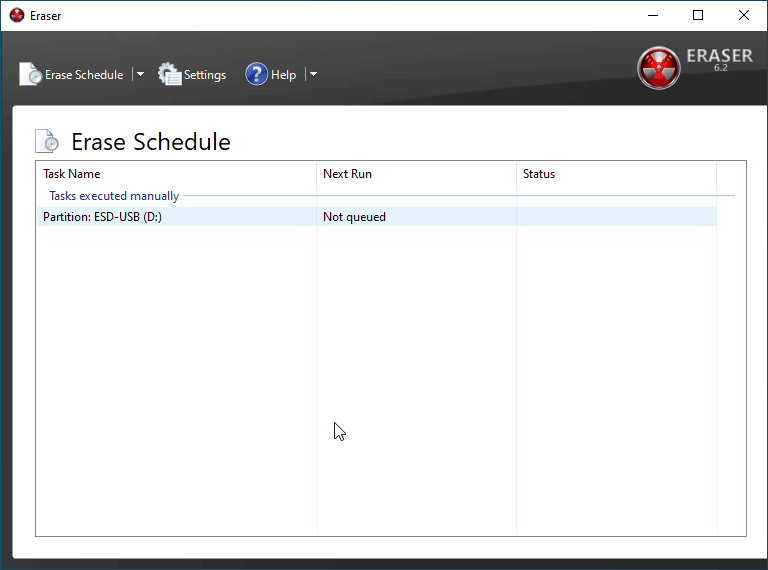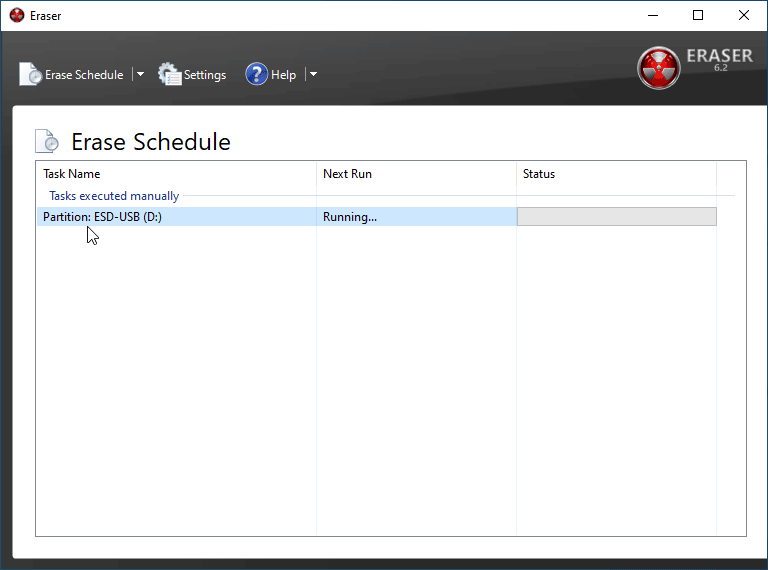
Click New Task and then Add Data on the task properties window that opens. This is where you'll be able to designate something to be deleted and how exactly you'd like it scrubbed from your drive.
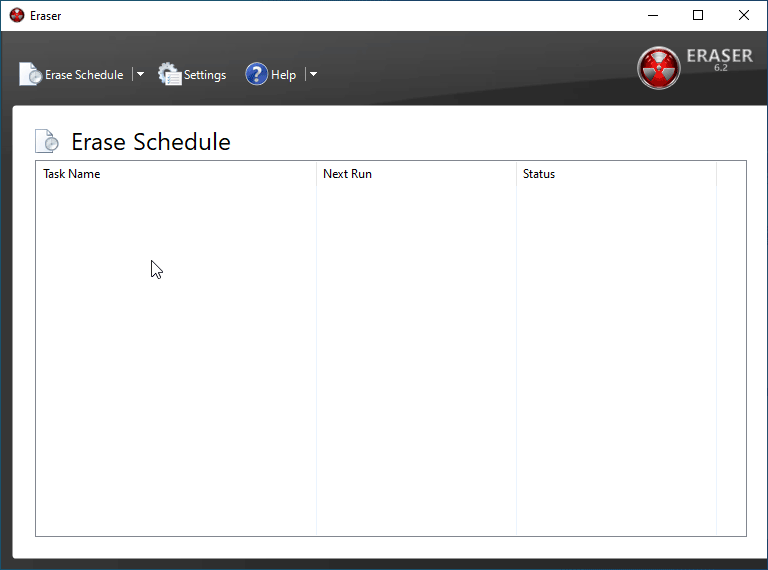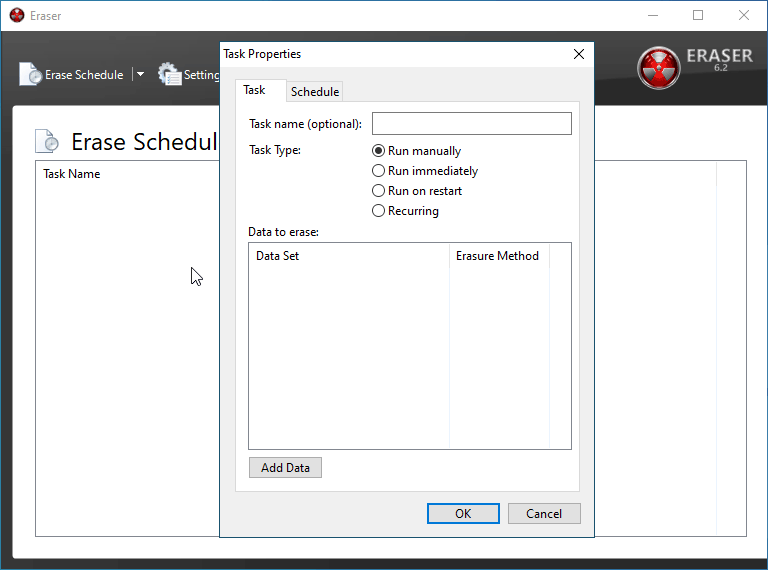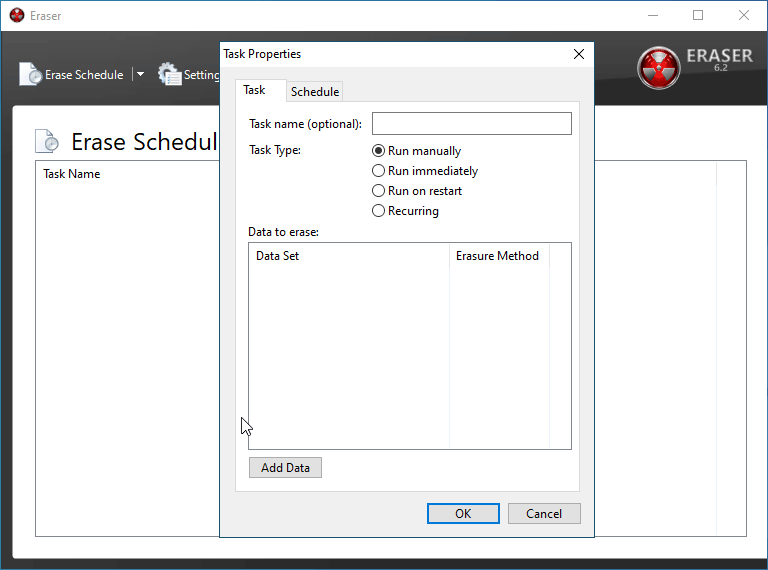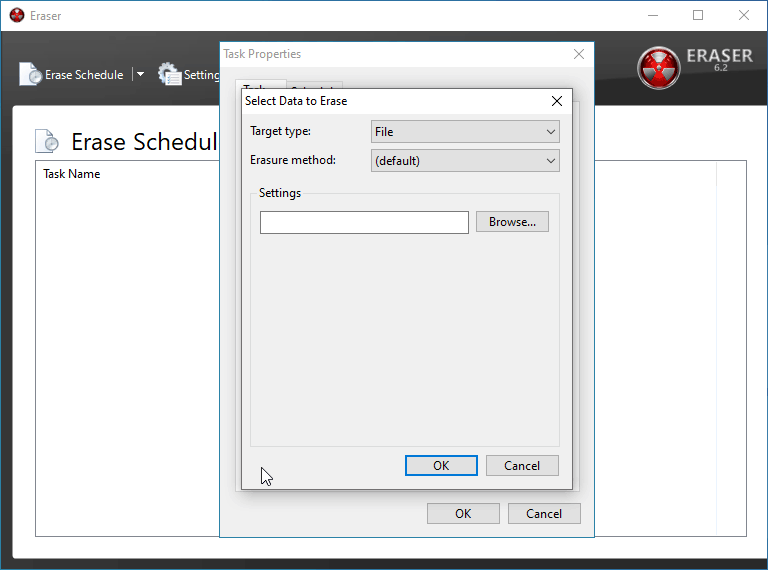
Depending on what you're trying to delete, you'll want to pick different things here. In this instance, I am doing a full wipe of a flash drive of mine.
I've also opted to use the Gutmann Method as it is the most secure option, but its also by far the lengthiest so feel free to use one of the other wipe methods such as the U.S. D.o.D method.
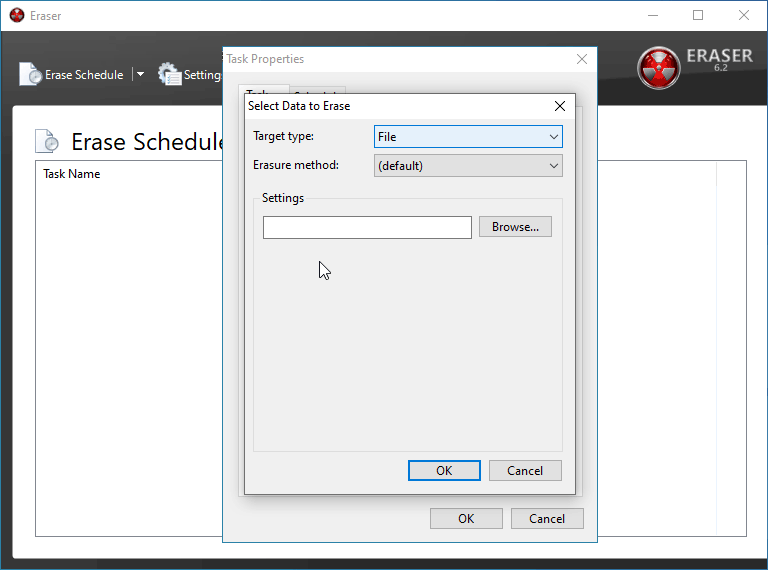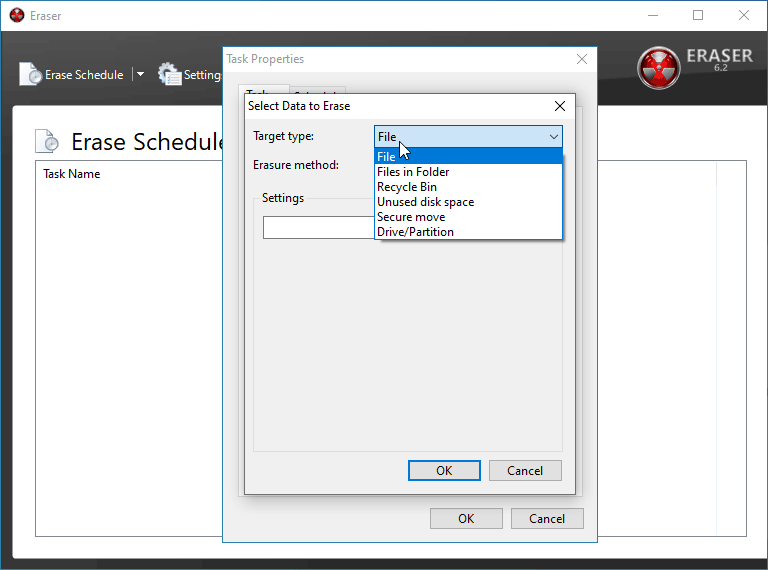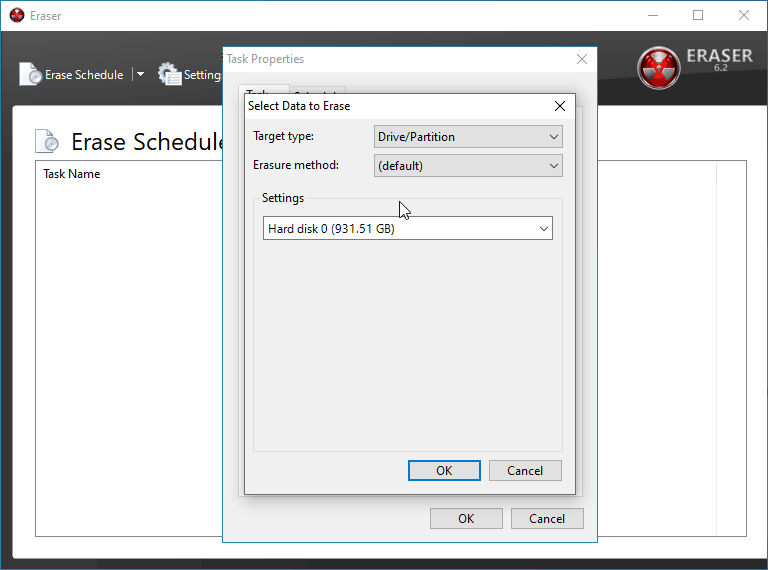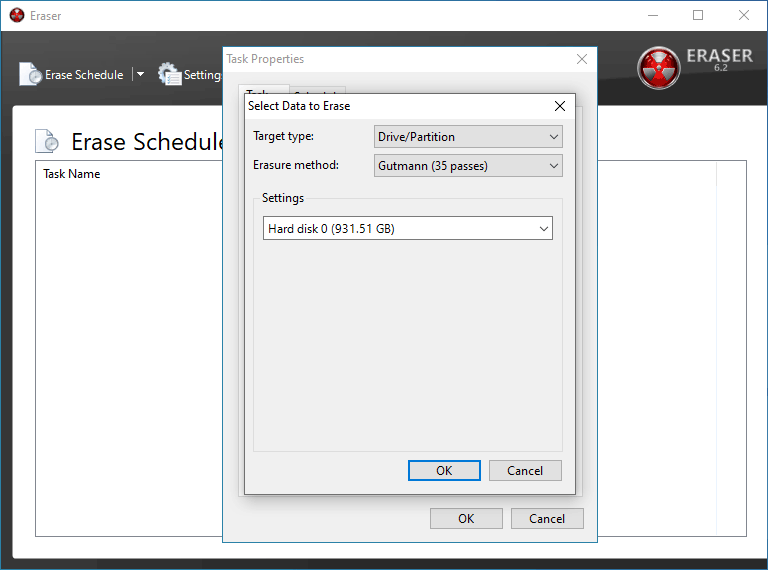
BE CERTAIN you have the correct device/folder/file selected in the box below before. If you move forward with the incorrect selection, you will be performing a secure delete on the wrong batch of data and you it will be close to impossible to recover it.
Once you've triple checked your selections, pres OK on both windows and return to the Erase Schedule window. If you've prepared all the files and devices you wish to delete, right click the selection and click Run Now. This will begin erasing process which, based on your location and method selection, can take a few seconds to several minutes.